Remote access scams have been a hot topic for years. The attack methodology is simple, but extremely effective. A scammer uses a trusted brand or entity, to convince the victim to provide remote access of their device to 'fix a problem'. The purpose is to evade fraud detection controls, as many banks treat sessions from a customer's normal device as trusted, and therefore low risk. Device ID profiling is therefore ineffective at detecting this type of fraud and losses are higher than ever, as seen in the latest ACCC Scamwatch statistics below:
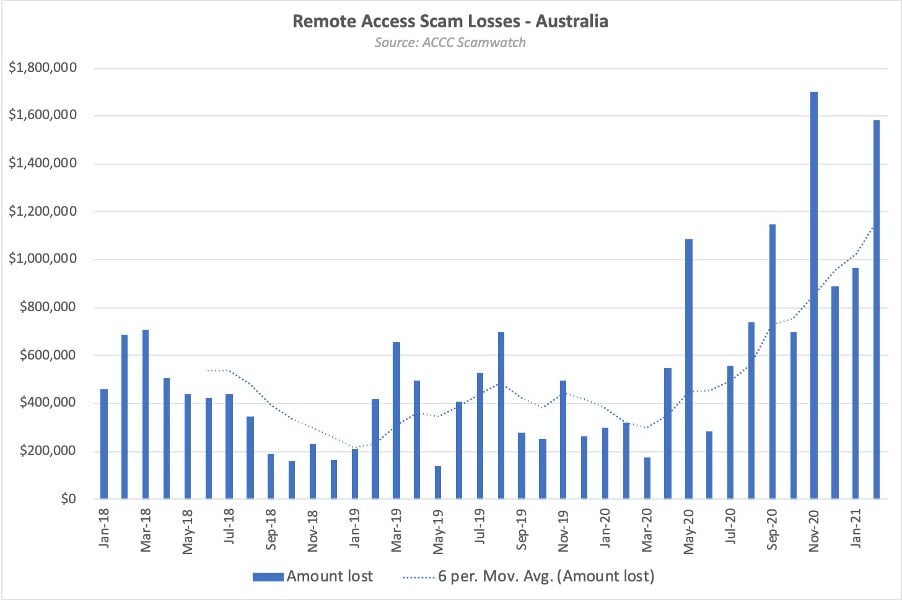
Historically, remote access scams have primarily been in the desktop environment, but in the last 12 months mobile has emerged as the platform of choice.
It makes sense when you think about it. The scammer is normally calling the victim on a smartphone device, so why not consolidate the attack onto that single platform. Smartphones are just small computers and many people now complete most (if not all) of their banking on mobile devices.
Let's step through a typical attack flow:
Step 1: Call a potential victim and convince them that they need to take immediate action to resolve a problem with their phone / banking / security. Criminals are now even using outbound IVRs to screen victims and connect only the most vulnerable potential victims to human scammers in a call centre (e.g. "press 1 to speak to a support agent").
Step 2: Instruct the victim to install a (legitimate) remote access or screen sharing app from either the Apple or Google Play app stores.
There are many to choose from, but let's choose TeamViewer QuickSupport, as it is a well-known support tool, that is available on both iOS and Android platforms. It is also feature rich and provides functions such as device information, remote access, taking screenshots, uninstalling apps, file transfer, stopping processes and chat. iOS is more locked down than Android, so it is limited to a subset of these functions.

Step 3: The scammer asks the victim to provide their relevant connection ID, so that they may connect remotely to the device and the real fun can begin. Let's take a look at this from the criminal's perspective:
The connection interface on the criminal's device
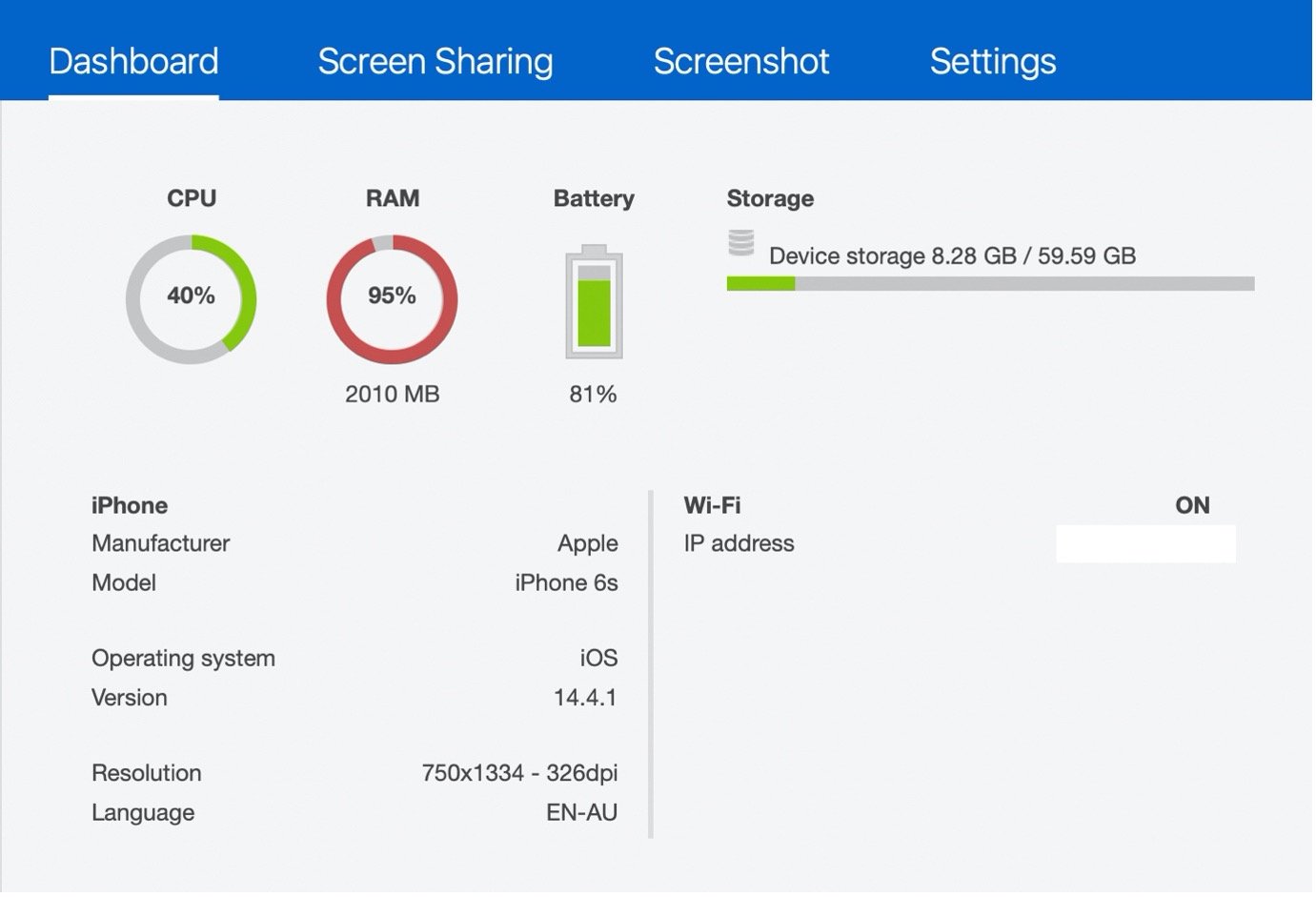
Ability to view device and network details of the victim's phone/tablet
The criminal guiding a victim through the scam
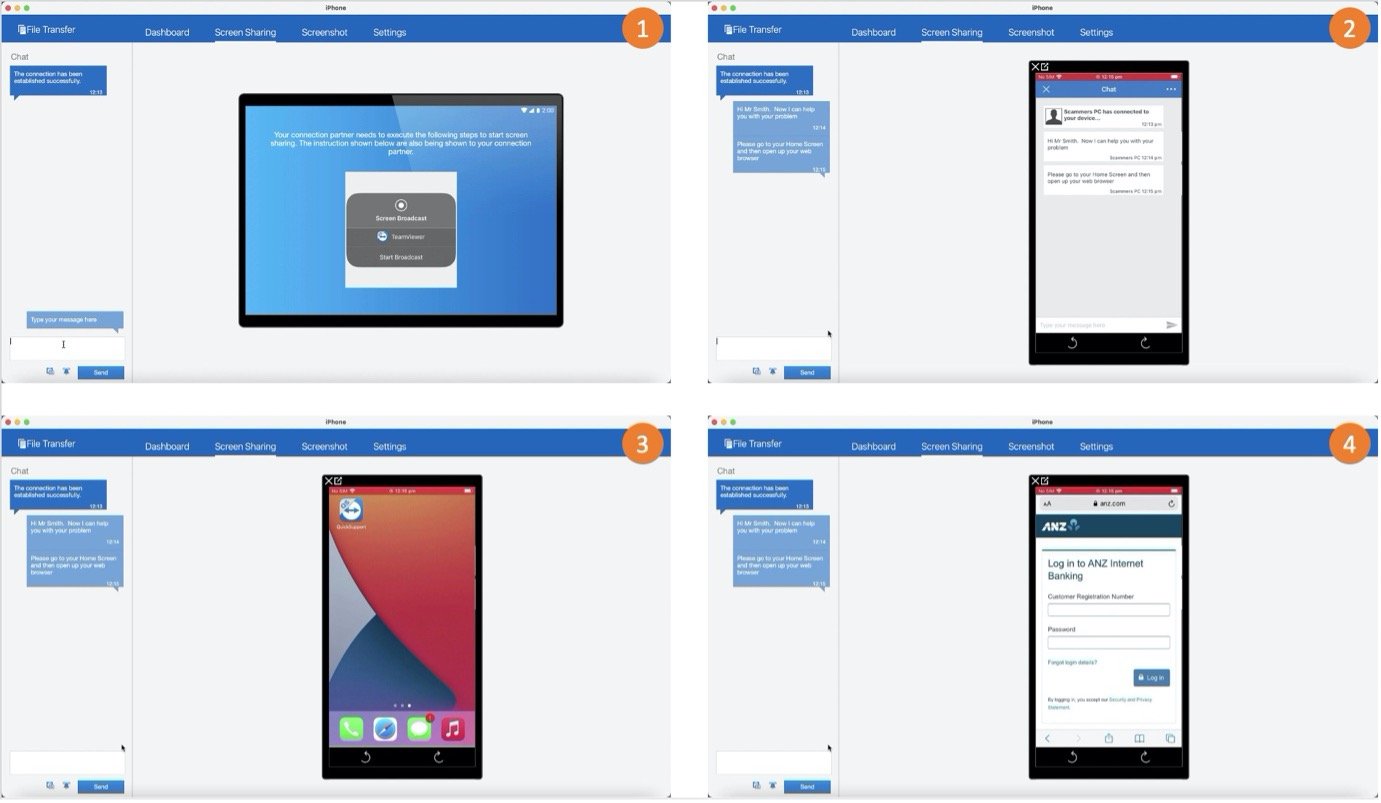
Step 4: Socially engineer the victim (distract, coerce, confuse, etc) to allow the attacker to transfer funds to a mule account. In the case of iOS, the device cannot be remote controlled by the attacker, so it requires some additional steps in convincing the victim to make the transfer themselves - but it is still very effective.
Step 5: Attack concludes. Funds have been stolen and the victim will eventually realise that they have been scammed. Whether or not they are refunded (as a victim of fraud), is usually down to the discretion of their specific bank. However, there is increasing pressure to reimburse victims, through initiatives such as the UK's Contingent Reimbursement Model and banking regulators such as AFCA.
One important point to understand is that it is not the remote support tool itself that is malicious. These tools solve important problems for those who need help with their technology, especially in the context of a global pandemic.
It is not all bad news though - this is a problem that can be solved for with smart technology. To mitigate this risk, banks must invest in deep behavioural profiling technology such as BioCatch, which is extremely effective at detecting mobile remote access and social engineering scenarios. Mobile remote access scams are certainly here to stay.
This article was originally published on LinkedIn by Tim Dalgleish, Head of Professional Services, APAC at BioCatch.



