Acquire new customers, not fraudulent accounts.
Ensure every new application is genuine — no roadblocks for real customers, no openings for fraudsters. Eliminate threats, accelerate trust, and protect your success.
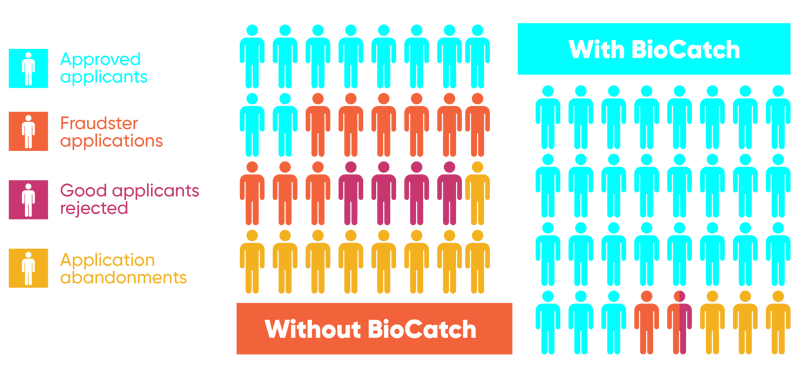
Stop fraud before it starts.
Whether it’s non-human activity such as bots, scripts, or emerging AI agents, or human fraudsters using stolen data, financial institutions face relentless, sophisticated account-opening attacks. BioCatch Account Opening Protection uses multi-signal telemetry including, behavioral, device, and network data, to expose stolen or synthetic identities, bots, and money-mule recruitment in real time, blocking criminals before they establish footholds for downstream fraud and money laundering.
Fraud never sleeps, neither should your defenses
BioCatch stops fraudulent account openings without compromising experience, driving more genuine accounts, higher revenue, and lower operational costs. Our multi-signal fraud defense scales effortlessly, maintaining a best-in-class customer experience.
$100M
in scam payments prevented by one regional bank in the U.S. in 2024
85%
decline in fraud attempts at a leading European bank
70%
reduction in fraud losses ($30 million AUD per year) at a leading Australian bank
70%
reduction in fraud losses (more than $4 million/year) at a top-10 bank in Latin America


