Another dark web takedown by the FBI has been realized and reported on recently. This time it was the Genesis Market which sold some of the more interesting items that are frequently available for sale to bad actors. This sensational part of the fraud space, the compromised data broker/stores, operate in this “fraud as a service” model as the industrialization of the space occurred and created some of the wilder elements of the story arc of banking fraud.
Dark market vendors have been working hard at meeting the needs of their customers these days. Long gone are the marketplaces that simply sell carding details, such as the 16-digit account number, expiration date and CVV2 details or “Dumps” of track 2 data. The growth in utility of this data started including more demographic details in association with payment details. Let’s do the how we got to now, and see what’s different about this most recent revelation and we can add a bit about what we see on the fraud side.
Time to hit rewind…
Somewhere amid the pre-EMV card era in the U.S, we started to see more of the demographic details of compromised cards get sold. This included location information of the compromise, as frequently, we could catch early card present fraud with “out-of-state” strategies and be more effective with our fraud detection rules and controls. Including the zip code of the breached terminal had better fraud conversion rates when the fraud occurred in the geographic footprint of the cardholder. The cost of these on a per card compromised basis was cheap, averaging $10-$20.
We also saw an increase in the sale of “Fullz” – fraudster terminology referring to a more complete dataset of an individual and their identity. These records offered a fairly comprehensive record of an individual’s dataset to include account numbers, login credentials, demographics and other relevant non-public personal information like Social Security number (SSN) and date of birth (DOB) which could be used in account takeover or account opening events. It contained login information which would be used to raid existing or fund novel accounts. This was quite a bit more expensive, sometimes 4-10 times the cost of card data only, and tended to be more limited in available volumes.
More recently, compromised card data, and especially that which was primarily card-not-present data, would be sold with a larger picture of the consumer so that data elements like the billing address could be leveraged. But something happened in the post-EMV era where SSN and DOB would be available, and at roughly the same price OR EVEN included in a compromised card sale. This started to reduce the cost of entry for a new smishing-scam type of attack, the impersonation scheme, which usually used the DOB and SSN, both common knowledge-based authentication elements to initiate an online banking password reset, and a card number to make the scam more convincing to the victim. A phishing message in this capacity may look like this:
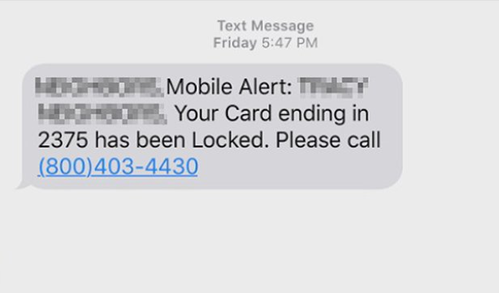
These attacks are still quite common and effective, have a low barrier to entry, and may even be of low sophistication so the conversion rates are likely not as high as they once were. With fewer people taking the bait, this paved the way for illicit storefronts, such as the Genesis Market, which has created a new threshold for exploitation of compromised data.
Genesis Market sold something very different. It was able to trade in the next exponent of Fullz. These compromised accounts had persistent access to the legitimate user’s device and its information that you used to log in to your favorite services. Websites and apps, like that of your favorite online banking destinations (among others and let your mind run wild), store software locally on your device in the form of cookies. These delicious tech snacks allow you to come back later and authenticate with lower levels of friction, making the session appear to be coming from your exact device, right down to the screen resolution of your display.
And yes, in practice, what we see at BioCatch is that the threat would be invisible to conventional authentication controls at login, but with additional monitoring of session elements, a new user becomes visible. In this session, there is evidence of a distinct and novel machine behind it, as well. Along with the monitoring of the rest of the user’s journey and the manipulation of specific non-monetary elements in the session, and then the setup for a future payment, detection and prevention is realized.
Ultimately, we’re more consistently recognizing that current authentication practices and methods are being consistently overcome, as people and machines are both exploitable. Having that back-end control point, to recognize and alert the moment when something has gone wrong, is now table stakes for maintaining control over your digital domains.



