Remote access scams are a very common scam type, where the victim is contacted by a criminal acting as a trusted third party (such as a tech company, telco or bank), and socially engineers the victim to provide access to control their device. Historically, these scams were PC/laptop based, but increasingly this is now a mobile problem also.
In 2022, the total losses reported to the FBI from remote access scams (also known as tech support scams) was $806 million. This was an increase of over 230% and nearly half a billion dollars compared to 2021. It was the third largest single contributor to reported internet crime losses, only behind investment and business email compromise (BEC).
These scams are effective, as they enable the attacker to proxy through the victim’s device and disguise their actions behind a trusted device and/or IP address. Many historical digital channel fraud controls have relied on knowing the customer’s normal device and IP address, so criminals have evolved their attack methodologies accordingly.
How to Combat Remote Access Scams
The good news for companies looking to protect both their business and their customers is that there are tools and techniques available to help address this problem.
Based on our experience working with companies across the last 10+ years, here are the top five tips to help combat remote access scams:
1. Behavioural biometrics
-
- Behavioural biometric data allows us to understand whether a device is being controlled locally (or not) by analysing mouse movements, keystroke behaviour and screen interactions throughout a digital session. BioCatch has been the leader in this research and protects over 5 billion banking sessions per month using this technology.
2. Call data
-
- Speaking on the phone while doing your banking is incredibly rare, and we observe this is in less than 1% of genuine sessions. However, during a remote access scam, a victim is on the phone while in session in up to 70% of cases, and this insight is a magic data point for scam detection purposes.
3. Integration with payment / KYC data
-
- Once we have access to both behavioural biometric and call data, it is extremely important to integrate this data with the traditional payment fraud systems. Knowing that a 65-year-old person making a $8,000 payment to a new recipient is not enough to make an accurate fraud decision. However, if we overlay behavioural biometric and call data, then we are in a very strong position to make an extremely accurate fraud risk decision.
4. Decline vs. hold
-
- Protecting the user experience of genuine customers is a key KPI of any fraud management team. We must be extremely accurate when making an ‘all or nothing’ payment decline due to fraud risk. An alternate approach is to allow the payment to superficially approve from the customer’s perspective but to quarantine the payment in the bank’s back-end payment systems. The benefit of this approach is that it provides a time window to both triage the event and contact the customer (once the scam call has ended – else their line will be busy).
5. Communicate and educate
-
- Educating customers about the risk of scams is an ongoing investment for any bank. Traditionally, much of this education has been static in nature and therefore consumers have largely become immune to such warnings. However, new innovations such as National Australia Bank’s in-session payment prompt messaging and Commonwealth Bank’s ‘CallerCheck’ are excellent examples of newly improved communication techniques. Other examples include the Singaporean government investing in an excellent Scam Alert website to educate their citizens on scams.
Working Hard to Reduce the Impact of Remote Access Scams
It is easy to make the case around the importance of these controls, but I hear you ask, “Where is the evidence that it will actually make a difference?”
Fortunately, we have case studies from around the world where banks have actively worked hard at reducing the impact of this scam type using a combination of the above-mentioned controls.
In Australia, throughout 2020-21, we observed a similar exponential growth in remote access scams losses as per the 2022 FBI statistics. Australian banks have worked hard to address this trend and we now are seeing the ‘green shoots’ of a positive downturn in the loss trend as outlined in the below chart.
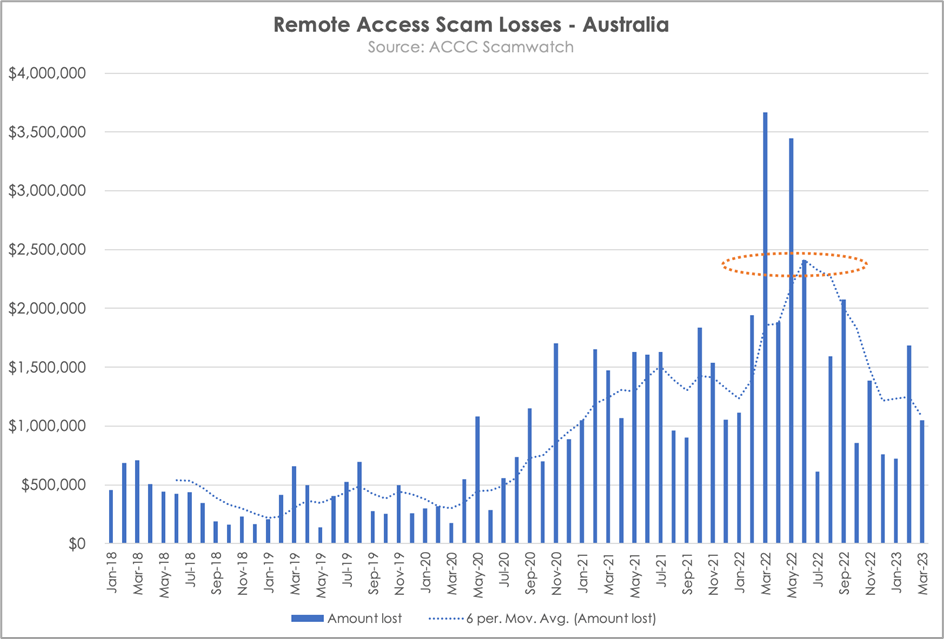
Conclusion
Remote access scams continue to be a major digital crime type impacting victims globally, as it is a very effective attack technique to bypass traditional digital channel fraud controls. However, with an investment in the right technology, processes, and communication, we can make a difference and turn the tide on the trend.
Additional Resources
Learn how remote access attacks are evolving, where legacy fraud controls are falling short, and how behavioural biometrics can provide the additional visibility banks need to prevent these attacks in the white paper, Winning the RAT Race: How Banks Can Get Ahead of Remote Access Attacks.



