The rapid growth and adoption of digital banking has led to surging fraud rates. And despite increased investments in fraud protection, financial losses remain at an all-time high, exposing gaps in traditional fraud prevention and authentication controls. According to PwCs 2020 Global Economic Crime and Fraud Survey, fraud cost participating organizations $42 billion over a period of 24 months1.
Exposing Weaknesses in Traditional Fraud Controls
Traditional controls such as 2FA or One-Time-Passcodes (OTPs) authenticate a user in context of a certain activity such as when a user attempts to login, transacts, or updates their account contact information. While these methods are important, cybercriminals have evolved to bypass such controls through social engineering and other means. This evolution has required organizations to layer up, leading to an increase in the adoption of additional device ID, location analysis, transaction monitoring, and behavioral analytics- based fraud prevention solutions. While these methods can provide greater security, their approach is often flawed in the way they analyze risk at a single point in the digital flow, such as at log in or point of payment, providing organizations with only a snapshot into fraud risk and a limited amount of data to base their decisions on.
Continuous Protection Using Behavioral Biometrics
To distinguish between genuine and criminal activity most effectively, continuous session visibility and risk analysis is key as many of today’s most sophisticated fraud threats, such as social engineering voice scams, can only be detected when carefully and continuously monitoring for subtle deviations in user behavior.
Contrary to traditional controls, continuous protection solutions passively determine whether a user is genuine throughout an entire session and proactively alert organizations in the event signs of fraud are detected. Further, instead of relying on static information, like IP, device ID, and location, continuous protection using behavioral biometrics verifies a user’s legitimacy based on their digital behavior. From log in to log out, continuous protection works in the background to analyze risk level based on thousands of behavioral features such as keystroke movements, mouse activity, and scrolling events.
As cybercriminals continue to evolve their tools and techniques to perpetrate fraud, what if organizations had the ability to unlock the power of behavior to predict fraud before it occurs?
Continuous Protection in Action
The reality is that fraud occurs over multiple sessions, providing a window of opportunity that can be taken advantage of with the right tools in place. When fraudsters engage in cybercrime within digital banking, they typically conduct log-in only sessions prior to making a transaction to validate a user’s credentials, verify funds, or gather information about the user or account to later manipulate the victim as part of a social engineering scam. In this scenario, the user doesn’t perform an action that will trigger risk analysis or additional authentication, flying under the radar of traditional controls. On the contrary, continuous protection solutions based on behavioral biometrics would see and alert on this activity, allowing organizations to act well before the fraudster is ready to make a payment.
Continuous protection in action would look like this:
- User logs into a web banking session by pasting their credentials
- User views the main account summary page
- The session eventually times out after 200 seconds
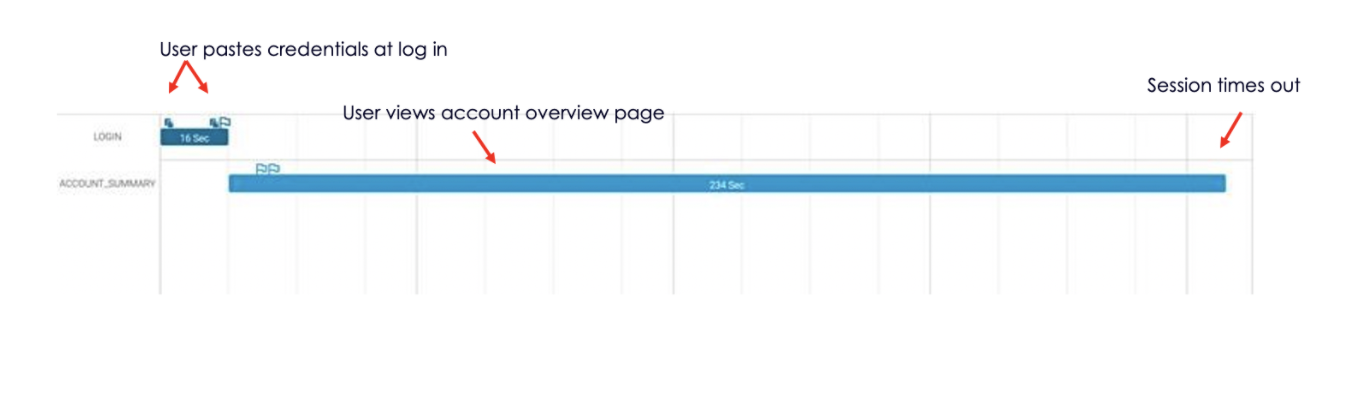
- The continuous protection solution observes all behavioral, device, location, and network elements available during the session and deems the session as high risk based on the following indicators and more:
- Low data familiarity with personal information (in this case, user credentials)
- Anomalous import activity (the user had no history of pasting their credentials in past sessions)
- Anomalous mouse, click, and wheel activity when compared to the user’s historical web sessions
- Device preference anomaly (user generally uses their mobile device for log-in only sessions)
- The user’s device was inconsistent with previous sessions and linked to four other user sessions occurring on the same day within minutes of each other, indicating five different customers were phished by the same campaign
- A proactive real-time API notification is sent to the bank, investigation immediately follows, and action is taken before the criminal can cause financial damage



