Phishing is the oldest weapon in a fraudster’s war chest and still serves as the most common form of cyber-attack around. Phishing attacks reached a record high in 2022, according to the Anti-Phishing Working Group, with banks continuing to be the number one target.
What has become known to many consumers is how to spot most phishing emails when they hit their inbox. For the few that are successful, what remains unknown, is what happens after a phishing attack? Some get lucky, and the theft of personally identifiable information (PII) amounts to nothing. It could be that sensitive information was stolen but never sold or purchased on the dark web. Or perhaps it IS purchased, but the fraudster doesn’t get around to attacking everyone on the list. Who knows?
Unfortunately, not everyone is lucky. Some individuals are attacked within 24 hours of their sensitive details being stolen. This is often the case when it comes to phishing sites, otherwise known as lookalike sites. If a customer enters their details into a phishing site and the fraudster captures their login details, they can easily access the customer’s bank account without triggering any alarms. And if the providing bank doesn’t have adequate fraud controls in place, they are free to empty a person's account and leave both the customer and providing bank with a huge headache to deal with in the morning.
BioCatch has been studying the tracks of fraudsters following early detection of phishing sites. Leveraging device and behavioural analysis, we can now shed some light on what happens after a successful phishing attack. Ok, let’s begin…
Recently, a large U.S. financial institution found itself the target of a massive phishing campaign. They were able to uncover this attack early leveraging the BioCatch Phishing Site Detection solution and in looking to understand the downstream impact.
127 victims unknowingly entered their full login details into the phishing site before it was shut down. Over the next two weeks, we observed the following activity within the 127 accounts:
30% went on to login from a location that was far away from their known location.
For example, with one particular victim, we could see that the legitimate user normally conducts login and payment sessions in New Zealand. But shortly after entering their login details into a rogue phishing site we suddenly started seeing logins from Florida. Subsequent login attempts then started happening in Boston suggesting the login details were being passed around from one fraudster to another. We can only speculate why the details were being passed around. Perhaps it was because some defensive measures kicked-in and the original fraudster was unable to make any further money transfers. So perhaps the access details were passed on to a fellow criminal to try and make more.
9% logged in from a location impossibly far away from their last login location, given the time in between sessions.
Sometimes, a login location can sit on the borderline of believability because it’s not too far away from the typical login location. This is where common sense and behavioral rules can prevail. By simply setting up a rule that asks the question - is this login location possible considering where the user last logged in at a particular time? This straightforward insight can give a bank much more confidence to intervene in a session and know you are not interrupting a legitimate session being conducted by the true owner of the account.
23% made a payment that was flagged as a high-risk amount.
There are many reasons a payment can be concluded as high risk. It could be because the payment is being made from an unusual location. It could be because the device being used to make the transaction is unfamiliar. Or it could be because the amount being transferred is not typical of previous behavior. In terms of the 127 accounts, it was a mixture of all of the above, particularly the sudden out-of-character large payment transfers going on within the accounts. With behavior in place, you are better positioned to intervene with these transactions. Stopping the money leaving the account and preventing the fraud altogether is a far better option than managing the fall-out with customers and fronting the potential fraud bills.
15% of the accounts were later flagged for the use of a Remote Access Tool (RAT).
RATs are commonly used by fraudsters to navigate around a customer's account from afar. Fraudsters can operate under the radar, remain anonymous and conduct fraudulent activities on the victim's device. Behavioral biometrics can identify the use of a RAT in a session by analyzing mouse movement patterns. The remote access connection can result in a jumpy, inconsistent mouse motion which looks quite different from a normal user.
12% pasted in the login fields for the first time.
Copying and pasting is a convenient keyboard shortcut we all use in our daily lives. However, in the context of filling in a new account application or logging into an existing account, the act of copying and pasting is highly suspicious. Why? Because legitimate users do not copy and paste their email addresses or other types of PII into an online form. This personal data sits in the owner's long-term memory bank and is typically typed in. There is only a benefit for a fraudster to use the copy and paste function in this context because they are NOT familiar with the data and it’s quicker to attack multiple accounts using the copy and paste feature.
These five telling insights extracted from the 14 days of activity after the 127 victims got fooled into sharing their data with a phishing site give us some indication of ‘what happens next?’ The data is further proof that phishing is just the beginning of a wider plan that is coordinated by multiple fraudsters working together on a global scale. So what can we do to combat these fraudsters and these lookalike phishing sites?
The Need for Speed
The above talks about the worst-case scenario. 127 customers were fooled into sharing their login details. And then a whole lot of interesting fraudulent activity happened soon after. However, as insightful as it all is, we’d all rather there was no fraudulent activity or victims at all. Unfortunately due to the relentless pursuit of fraudsters, this is not easily achieved. The best-case scenario is to turn the 127 victims into a small handful of victims by taking the following quick preventative measures:
STEP 1: Learn about the existence of the phishing site, quickly!
STEP 2: Take the necessary steps to get the phishing site shut down, quickly!
STEP 3: Alert the victims they need to update their login details, quickly!
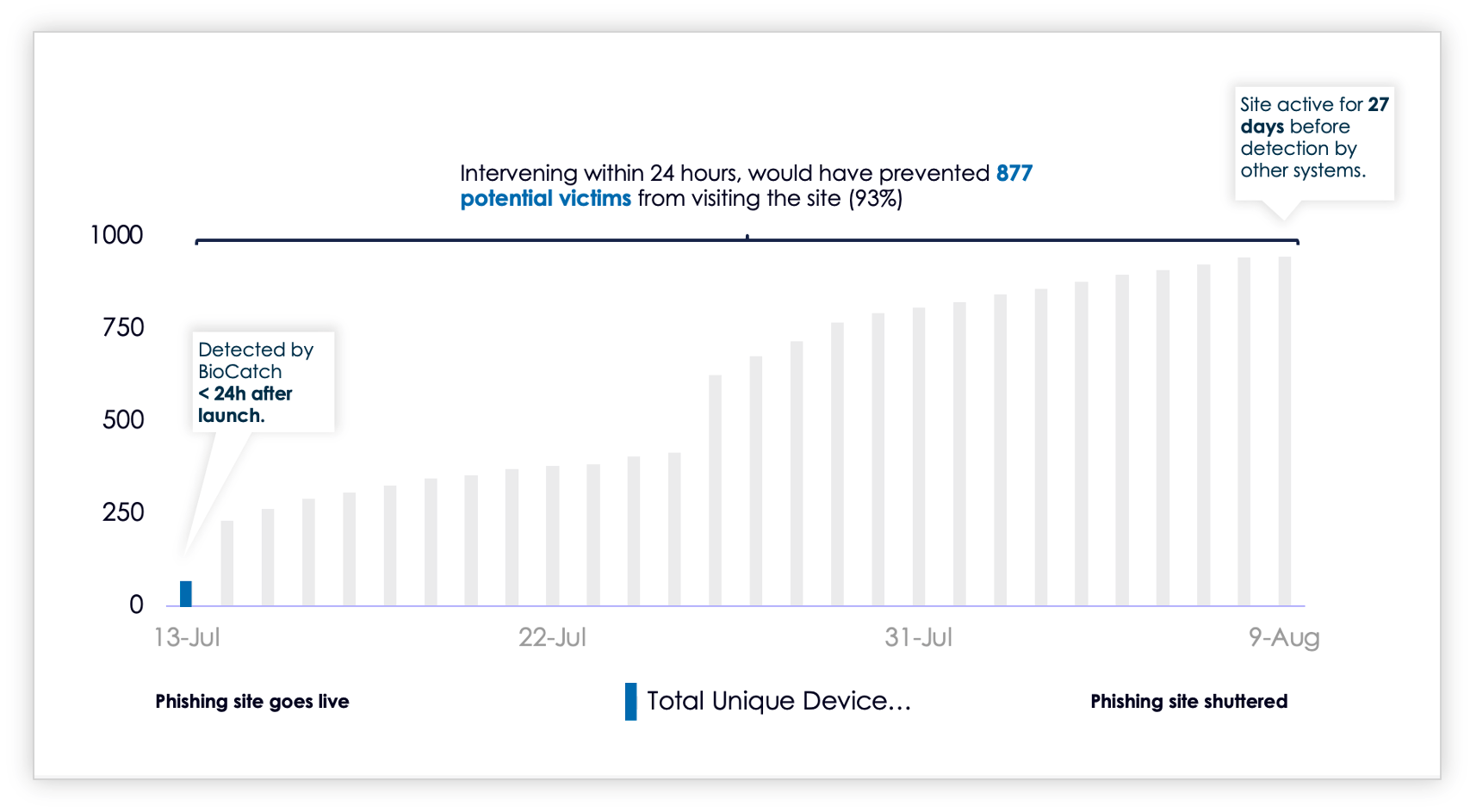
At BioCatch, we know these simple three steps make a lot of sense. Some insight obtained from another large financial institution we work with gave us an idea of the value of acting quickly. In the case of one phishing site, the analysis showed us that in the 27 days it took existing fraud controls to detect the site and get it shut down, the phishing site obtained another 877 victims after the initial 24 hours of creation. The handful of victims in the first 24 hours turned into hundreds in a matter of days and the potential clean-up process became a much larger job.
Stem the Flow of Account Takeover Fraud with Phishing Site Detection
In a similar way, fraudsters regard phishing as one part of a fraud strategy. Phishing site detection should form one part of an organization’s fraud prevention framework. When it comes to securing your customer’s accounts, stopping fraud at the time of account origination is a strong start. But you can do more by looking at how to protect them upstream (and downstream) as well. It's impossible to stop everything, but if you optimize your account takeover defenses with phishing site detection, fewer fraudsters will make it into the customer's account where they can go on to commit more severe types of fraud. Learn more about how phishing is most often the start of a more advanced attack down the line. Access the white paper, Four Ways Financial Scammers are Getting Ahead, to explore the top digital fraud threats in 2022, the limitations of existing fraud controls and how financial institutions are fighting back.



