In the last two decades, the use of biometric security applications has catapulted alongside digital innovation. This is due in large part to digital transformation in traditional industries, identity-based functions shifting to mobile applications, and a steep rise in fraud and identity theft in new digital channels.
According to forecasts by Acuity Market Intelligence, 98% of all smart mobile devices in use will be biometrically enabled. Moreover, Accuity’s research has stated that more than 16.7 billion biometric apps will be downloaded annually, and more than 1.37 trillion transactions, that require some level of biometric authentication, will be processed on mobile devices each year.
The Rise of Static Biometric Authentication Through Physical Characteristics
If you do your banking through a mobile device or transfer funds through any type of payment application, you’ve almost certainly experienced authentication through your physical characteristics. These are static, highly resistant to alteration, non-transferable and cannot be misplaced or forgotten.
Characteristics like fingerprints, face recognition, hand geometry, voice recognition, palm vein recognition, retina scans, iris recognition, and signature verification are the most common types of characteristics used for biometric authentication.
- Fingerprints: Through optical/ultrasound/thermal sensors, fingerprints can be digitally collected and stored. Fingerprints are considered the most popular biometric identification method and have been in extensive use for more than a century. The most widely used technique, minutiae-based matching, compares the location and direction of minutiae points. Each fingerprint contains 30 to 40 minutiae points and no two people have more than eight points in common.
- Facial Recognition: Using statistical patterns, facial recognition measures different points on an individual’s face to extract data and match them to pre-existing templates associated with the individual to verify his/her identity.
- Iris Recognition: These systems use special sensors to identify the iris and map segments into vectors, which include spatial and orientation data. This data is converted to a unique code and compares it to other stored codes.

The underlying assumption in the biometric security approach is that biometric factors are unique, measurable and consistent. Thus, in a wide array of technological systems, physical biometrics are used as the primary method for identification/ authentication and access control.
In a nutshell, biometric systems are based on three pillars:
- Sensors: subcomponents that detect and measure biometric data and digitize it.
- Templates: signal processing algorithms and techniques create biometric templates of the user. Later, these templates are compared to stored data and matched with existing profiles.
- Decision Rules: a decision process that uses matching event results.
The Rise of Static Biometric Authentication Through Physical Characteristics
While the use of static biometrics has increased over the years, a growing number of companies and organizations have raised serious concerns about the use of physical factors.
- First, using only one physical biometric data point to authenticate a user at the time of login is fundamentally the same as adding a static second password; albeit one that can never be changed if compromised.
- Second, physical biometrics can be captured, and in many cases sold, used again or synthesized with fake IDs.
- Third, there are concerns around bias, which has caused large organizations like IBM to withdraw or scale back from facial recognition technologies. Gartner’s Market Guide for Identity Proofing and Affirmation highlighted that "An increased awareness of bias in machine-learning-based systems reveals that the facial recognition algorithms used in an important class of identity-proofing products have demonstrated demographic bias in their performance."
- Finally, physical biometrics are based on a static approach.
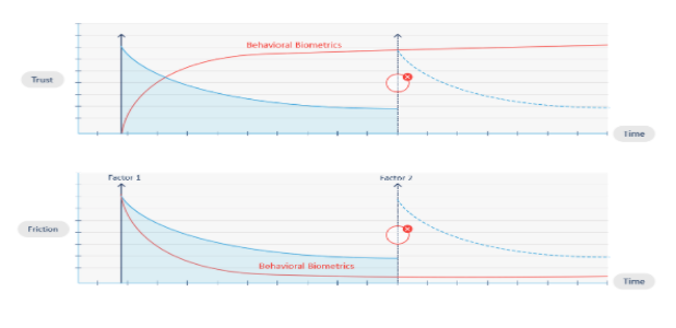
The problem with static biometrics security based on factors, like points captured in fixed images, is that even if the initial authentication is valid and done by the legitimate user, the integrity of the session gradually erodes over time. The only way to restore it is to require additional authentication factors.
However, continuing to ask users for traditional factors like fingerprints, facial recognition and passwords is disruptive and causes significant friction, leading to a poor customer experience. Businesses can’t ignore this. Up to 15% more revenue is available for digital businesses who have adaptive customer experiences linked to trust and risk assessments. In today’s digital world, users not only expect, they demand, to be able to access their bank accounts and payment applications as seamlessly as possible.
So, how do companies stay competitive and improve the digital banking experience while still keeping customers secure? The optimal solution is behavioral biometrics, a dynamic solution, rather than a static one, that increases trust and reduces friction during online sessions while also providing high levels of fraud detection. Behavioral biometrics run continuously in the background to protect sessions post-login and to detect subtle anomalies based on risk.
Behavioral biometrics analyzes an online user’s physical and cognitive digital behavior. It has emerged as a breakthrough cybersecurity technology that identifies people by how they do what they do, and identifies behavior patterns of legitimate users vs human or non-human cybercriminal actors. It is an advanced solution for fighting cybercrime and detecting fraud in an age when criminals have more access to our personally identifiable information (PII) and more sophisticated hacking methods than ever before.
Cyber attackers are becoming much more sophisticated, and our reliance on digital services is increasing, especially during the COVID-19 pandemic. Security measures must get smarter to both detect new forms of cybercrime and support the growth of digital channels. Many experts and market leaders agree: behavioral biometric profiling is the only effective way to achieve this level of security.
How did biometrics evolve to where we are today? In our next blog, we will discuss the evolution of behavioral biometrics technology, how it works today, and what the future will hold.
Want to learn more about BioCatch’s behavioral biometrics solution and how we provide a secure and seamless digital experience? Read our solution brief to learn about BioCatch’s approach to Advanced Behavioral Biometrics.




